Data classification software that helps you lock down critical data
The variety of ways organizations create, store and share data is mind-blowing, making it harder and harder for you to identify what need to be protected. Netwrix Data Classification enables you to accurately identify and classify sensitive and business-critical content across your organization, therefore mitigating the risk of data breaches and satisfying compliance requirements with less effort and expense.
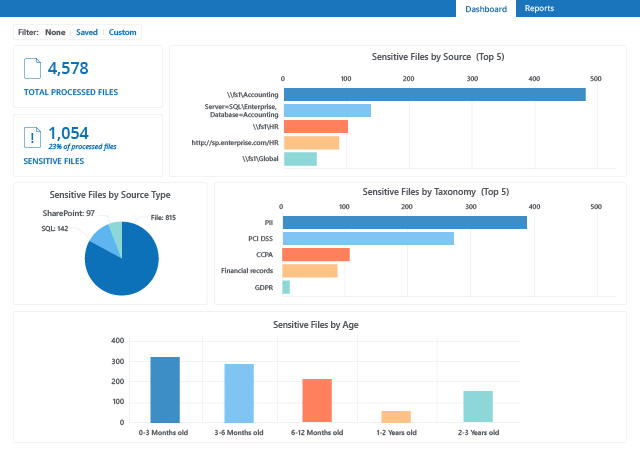
Get a focused view of your sensitive data across data stores
Want to gain complete visibility into what content you have, whether it’s structured or unstructured data, on premises or in the cloud? The Netwrix data classification solution has your back.
Classify data accurately and focus your data protection efforts

See how Netwrix helps organizations from different industries overcome their data security and compliance challenges

The solution provides a wide set of predefined taxonomies that cover PII (GDPR), PHI (HIPAA), payment card data (PCI DSS), financial records and other types of protected information, so you can quickly find sensitive and regulated data and implement required security controls.
.jpg)
.jpg)


