Complete visibility into Group Policy changes and the current state of your GPOs
Group Policy Auditing Software
Netwrix Auditor delivers complete visibility into changes made to Group Policy objects, such as security settings and links between GPOs and domain controllers or public key policies, and enables you to compare their current states with your known good baseline, so you can facilitate Group Policy auditing, improve IT security and prove regulatory compliance more easily.
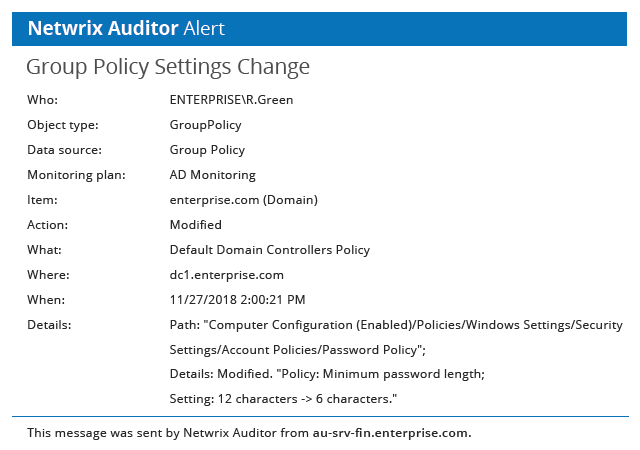
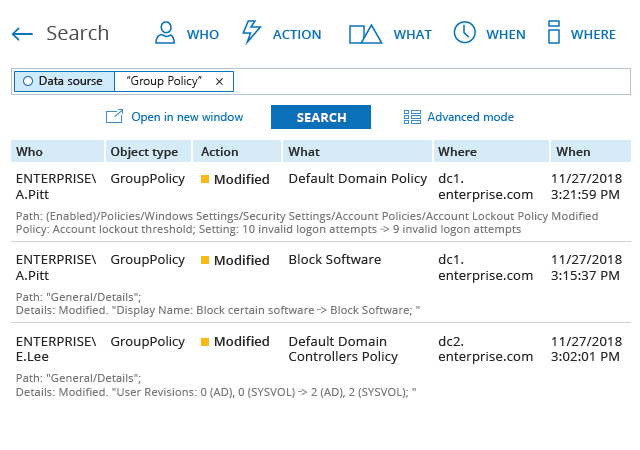
Monitors modifications to audit policy configuration and other Group Policy changes, providing the critical who, what, when and where details and before and after values.
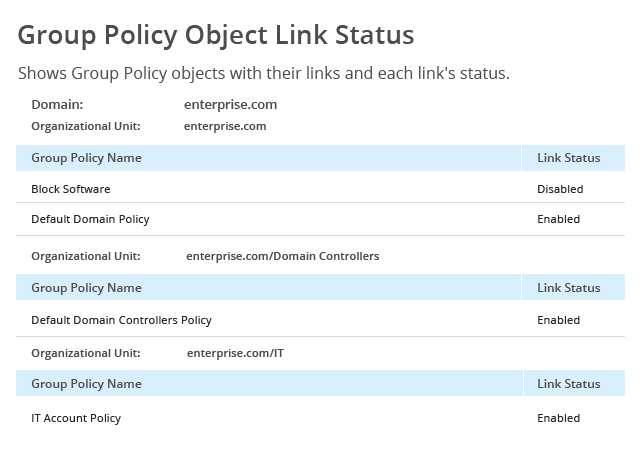
Shows the current state of your Group Policy objects and their settings, so you can easily compare them to a known good baseline.
Notifies you about critical changes to Group Policy settings, such changes to interactive logon policy or Windows settings, so you can respond immediately.
"Netwrix Auditor is a fantastic solution that has become a proxy set of eyes and ears, monitoring the network for anomalous Active Directory and Group Policy activity. The volume of information it sorts through would require someone spending 4–8 hours per week. At the rate I pay for MSP support, that equates to a savings of $1,200–$2,400 per month in additional labor cost."

EventLink